In today’s digital age, managing multiple usernames and passwords for different online platforms and services can be a hassle. As the complexity of security and data privacy grows, so does the need for a more streamlined and secure way to manage authentication across platforms. One such solution is Single Sign-On (SSO), which is revolutionizing how users interact with digital systems. But what exactly is an SSO ID and how does it work? In this article, we will break down the concept of SSO ID, its benefits, how it works, and its significance in enhancing security.
What is an SSO ID?
An SSO ID is an identity created as part of a Single Sign-On (SSO) system that allows users to access multiple applications or services with a single set of login credentials. The idea behind an SSO ID is to simplify user authentication, so you don’t need to remember a different password for every system or service you use.
For example, think about how you can log in to your Gmail account, and within the same session, access Google Drive, YouTube, Google Docs, and other Google services without having to log in separately to each one. This is made possible because of Single Sign-On (SSO).
How Does an SSO ID Work?
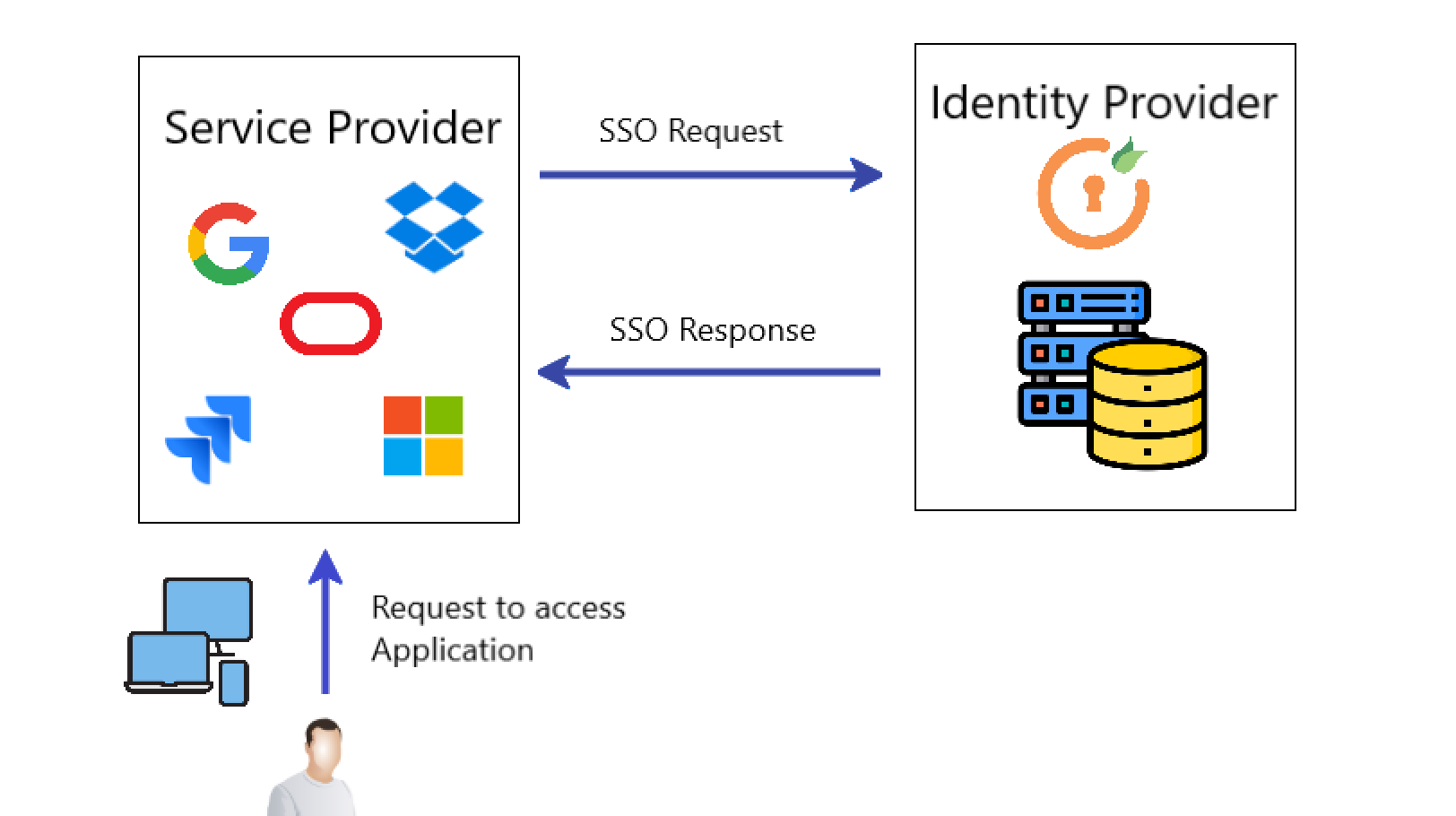
SSO works by creating a centralized authentication system where users log in once and gain access to multiple resources without having to authenticate each time. When a user logs into the SSO service, the system generates a token that confirms the user’s identity. This token is then shared across all other systems or applications that the user needs to access.
Here’s a simplified step-by-step process of how an SSO ID works:
- Login Attempt: The user attempts to access a resource (website, application, etc.).
- Redirect to SSO Service: If the user is not authenticated, they are redirected to the SSO login page.
- Authentication: The user enters their credentials (username and password) into the SSO system.
- Authentication Token Creation: The SSO service generates a secure token that confirms the user’s identity.
- Token Verification: The application or service verifies the token with the SSO provider.
- Access Granted: If the token is valid, the user is granted access to the application without needing to log in again.
Benefits of Using an SSO ID
- Simplified User Experience: The main advantage of SSO is that users only need to remember one set of login credentials. This reduces password fatigue and the chances of password-related issues, such as forgotten passwords or weak passwords.
- Increased Security: With fewer passwords to remember and manage, the chances of users reusing weak passwords across multiple platforms are reduced. Additionally, since SSO systems typically require strong authentication (e.g., multi-factor authentication), they provide an additional layer of security.
- Time-Saving: For users, the time spent logging in multiple times to different services is eliminated. This is especially beneficial in organizational settings, where employees can access a variety of services without having to log in repeatedly.
- Centralized Control: For organizations, SSO simplifies user management. IT administrators can centrally manage access rights and ensure that users only have access to the tools and services they are authorized to use.
- Reduced IT Costs: Because users experience fewer login issues, the number of password reset requests is drastically reduced. This leads to fewer calls to the help desk and, as a result, reduced IT support costs.
Common SSO ID Implementations
- Enterprise SSO: In businesses and organizations, SSO IDs are commonly used to manage employee access to internal resources like email, HR systems, databases, and cloud services. A centralized IT department configures access permissions and manages user accounts.
- Federated SSO: This form of SSO allows organizations to extend their SSO capabilities to external services and applications. For example, users can use their corporate login credentials to access third-party platforms such as Microsoft Office 365, Salesforce, and other partner services.
- Social Login: Social media platforms like Facebook, Google, and LinkedIn offer users the ability to log in to external websites using their social media accounts. These social login systems rely on SSO mechanisms to provide a seamless authentication experience.
- Cloud SSO: With the rise of cloud-based applications, SSO has become critical for organizations that use cloud platforms like Google Workspace, Microsoft 365, and others. Cloud SSO ensures users can authenticate once and access a variety of cloud applications without needing multiple passwords.
SSO ID Security Features
- Multi-Factor Authentication (MFA): Many SSO systems incorporate multi-factor authentication as an added layer of security. MFA requires the user to authenticate using more than just a password. For example, in addition to entering a password, users might have to provide a fingerprint or a one-time passcode sent to their phone.
- Encryption: To ensure that sensitive user data is protected, SSO tokens and authentication credentials are often encrypted. This ensures that even if an attacker gains access to a token, it cannot be read or reused.
- Token Expiry: The tokens issued during an SSO session have an expiration time. This reduces the risk of unauthorized access, as attackers would not be able to use an old token to authenticate.
- Audit Logs: SSO systems keep logs of all login attempts, providing organizations with a trail of user activity. This helps organizations detect and respond to suspicious login attempts and ensure compliance with security policies.
Challenges of Using SSO IDs
While SSO IDs offer many benefits, there are also some challenges associated with their use.
- Single Point of Failure: Since SSO is centralized, if the SSO provider experiences downtime or a breach, it could affect access to all linked applications. This makes it crucial to have robust backup and recovery systems in place.
- Security Risks: While SSO reduces the number of passwords users need to manage, it also means that a compromised SSO account could give attackers access to all associated applications. Organizations must implement strong security policies, such as MFA and continuous monitoring.
- Complexity in Integration: Integrating SSO with various applications and services can sometimes be complex, especially when dealing with legacy systems that are not designed for modern authentication protocols like OAuth or SAML.
- User Privacy Concerns: Some users may have privacy concerns about their identity being stored and managed by a central authority. Transparent data policies and informed consent can help address these concerns.
SSO ID recovery
SSO ID Recovery is a critical process for users who have lost access to their Single Sign-On (SSO) account credentials. Recovery typically involves verifying the user’s identity through alternative methods, such as email verification, security questions, or multi-factor authentication (MFA). In most systems, users are provided with a password reset link or a temporary access code to regain control of their account. For organizations, having a secure and efficient SSO ID recovery process is vital to ensure that users can quickly regain access to critical applications without compromising security. Regular audits and backup recovery options also help minimize downtime and prevent unauthorized access during the recovery process.
Conclusion
An SSO ID is an essential component of modern identity management systems that simplifies and secures the process of logging into multiple platforms. By reducing the need for multiple passwords and providing robust authentication measures, SSO enhances both the user experience and security. While there are challenges associated with its use, the advantages of SSO make it an invaluable tool for businesses, educational institutions, and individuals who want to streamline access to their digital resources.